AWS Architecture: Engineering for Security and Scale
A deep dive into cloud architecture patterns for autonomous security systems
System Overview: Hybrid Local-Cloud Architecture
The architecture was designed as a hybrid system to balance rapid development velocity with production-grade security standards. Rather than deploying the agentic core directly to AWS Lambda during the research phase, I containerized the application using Docker to run locally while maintaining direct, secure integration with cloud-native services (DynamoDB) for data persistence.
This approach decouples the compute layer (Local Docker) from the storage layer (AWS DynamoDB), allowing for zero-cost compute iteration while simulating a production environment where the agent operates with strictly scoped cloud permissions.
A. Identity & Access Configuration
To ensure the local agent adhered to the Principle of Least Privilege, I avoided using the root account or broad administrative credentials. Instead, I provisioned a dedicated IAM User specifically for the research agent.
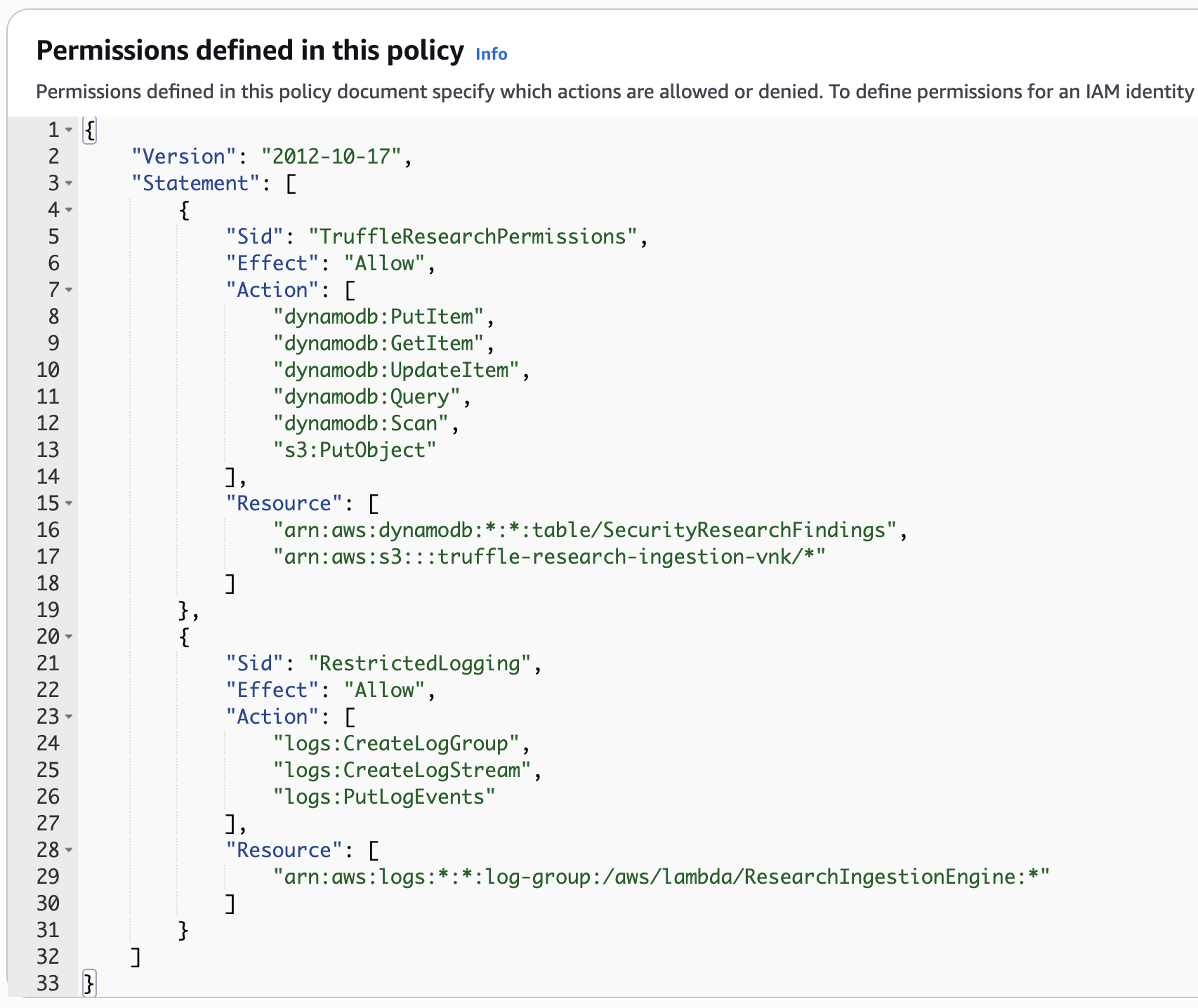
Step 1: Creating the Restricted IAM User
I created a user named truffle-research-agent and attached a custom inline policy that grants
scoped Read and Write permissions on the SecurityResearchFindings DynamoDB table.
B. Secure Credential Management
Hardcoding credentials is a critical security vulnerability (CWE-798). To secure the agent's access to the AWS
environment, I utilized system-level environment variables for AWS_ACCESS_KEY_ID and
AWS_SECRET_ACCESS_KEY.
Step 2: Runtime Credential Injection
By injecting these variables at runtime and strictly excluding them from the source code and version control
systems (via .gitignore), I maintained a high security posture that prevents credential leakage.
The application logic retrieves these values using os.environ, ensuring that no sensitive keys
exist in the codebase.
[Insert Screenshot: Terminal or IDE showing the .env file setup (with keys blurred) or the export commands]
Configuration of environment variables ensures credentials are never committed to version control.
C. Containerized Deployment
The application was packaged into a Docker container to ensure environment parity between the development machine and any future cloud deployment targets (such as ECS or Fargate).
Step 3: Building and Running the Agent
I used a multi-stage Dockerfile to build the image, keeping the footprint small. The agent is initialized
using a docker run command that passes the secure environment variables directly into the
container's runtime.
[Insert Screenshot: Terminal window showing the 'docker build' and 'docker run' commands executing successfully]
Executing the containerized agent with runtime variable injection.
Serverless Data Persistence: High Performance NoSQL Design
Implementing DynamoDB for Low Latency Storage of Security Findings
[Content to be added: Discuss DynamoDB table design, partition key selection, sort key strategy, and performance characteristics for security data retrieval.]
Overcoming the One Megabyte Scan Limit Through Recursive Pagination
[Content to be added: Explain the recursive pagination implementation, handling LastEvaluatedKey, and ensuring complete dataset coverage without missing critical vulnerabilities.]
Data Layer Efficiency: Using Projection Expressions to Reduce Context Noise by Sixty Percent
[Content to be added: Detail how projection expressions filter data at the storage layer, the specific attributes selected, and the performance impact on context window utilization.]
Identity and Access Management: The Principle of Least Privilege
Designing Granular IAM Roles for the Research Agent to Prevent Lateral Movement
[Content to be added: Describe the IAM role design, specific permissions granted, and how the role prevents privilege escalation and lateral movement.]
Implementing Resource-Based Policies on the DynamoDB Table to Restrict Access
[Content to be added: Explain resource-based policies, their role in defense-in-depth strategy, and how they complement IAM role permissions.]
Securing the Execution Boundary: Segregating Tool Logic from the Core Reasoning Engine
[Content to be added: Discuss architectural separation between reasoning and execution, security boundaries, and isolation mechanisms.]
Governance as Code: Automated Financial Circuit Breakers
Integrating AWS Budgets with SNS and Lambda for Real Time Monitoring
[Content to be added: Explain the budget monitoring architecture, SNS topic configuration, Lambda trigger setup, and alerting mechanisms.]
The AWSDenyAll Kill Switch: Implementing a Programmatic Safety Net for Cost Control
[Content to be added: Detail the kill switch implementation, policy attachment logic, triggering conditions, and failsafe mechanisms.]
Policy-Based Enforcement: Ensuring the Agent Remains Financially Bounded During Autonomous Research
[Content to be added: Discuss policy enforcement mechanisms, budget thresholds, and how the system maintains financial constraints during autonomous operation.]
Observability and Deployment: Monitoring the Agent Loop
Logging Agentic Traces via CloudWatch for Post-Incident Auditability
[Content to be added: Explain CloudWatch logging strategy, structured logging format, trace capture, and how logs enable post-incident investigation and debugging.]
Deploying the Frontend via Streamlit While Securing Environment Variables and API Keys
[Content to be added: Discuss secure deployment practices, environment variable management, secrets handling, and API key protection in the Streamlit frontend.]